Microsoft Entra ID is primarily an identity system for Microsoft applications and services. However, you can also integrate other applications and services with Microsoft Entra ID. And it’s even highly recommended, because you get single sign-on using corporate identity, you don’t have to maintain another separate user account system, you have the ability to apply conditional access policies to these external applications and services, etc.
User consent to Entra ID enterprise applications
But the problem is that by default, even a regular user can give consent to an external application to access Microsoft Entra ID and other services tied to it. This is very risky as it can lead to leakage of sensitive internal information as such applications can have arbitrary permissions that the user gives the application access to.
Typical examples are email clients – a user gives permission to an application (email client) to access an account, but for the application to perform its role, it must by definition have access to all of the user’s emails, typically also contacts, calendar, etc. If such an application were to be malicious, a threat actor could easily gain access to all of the user’s data.
And unfortunately, these are things that commonly happen. For trusted apps, for example, this is not such a problem, as, for example, Apple is not expected to exfiltrate user data within its Apple Mail app.
Entra ID enterprise application risks
But the much bigger problem is downright faulty apps. Very often these are apps that masquerade as other well-known and trusted apps. The user then gives the app access in good faith, usually without even reading what permissions the app is asking for, and grants access.
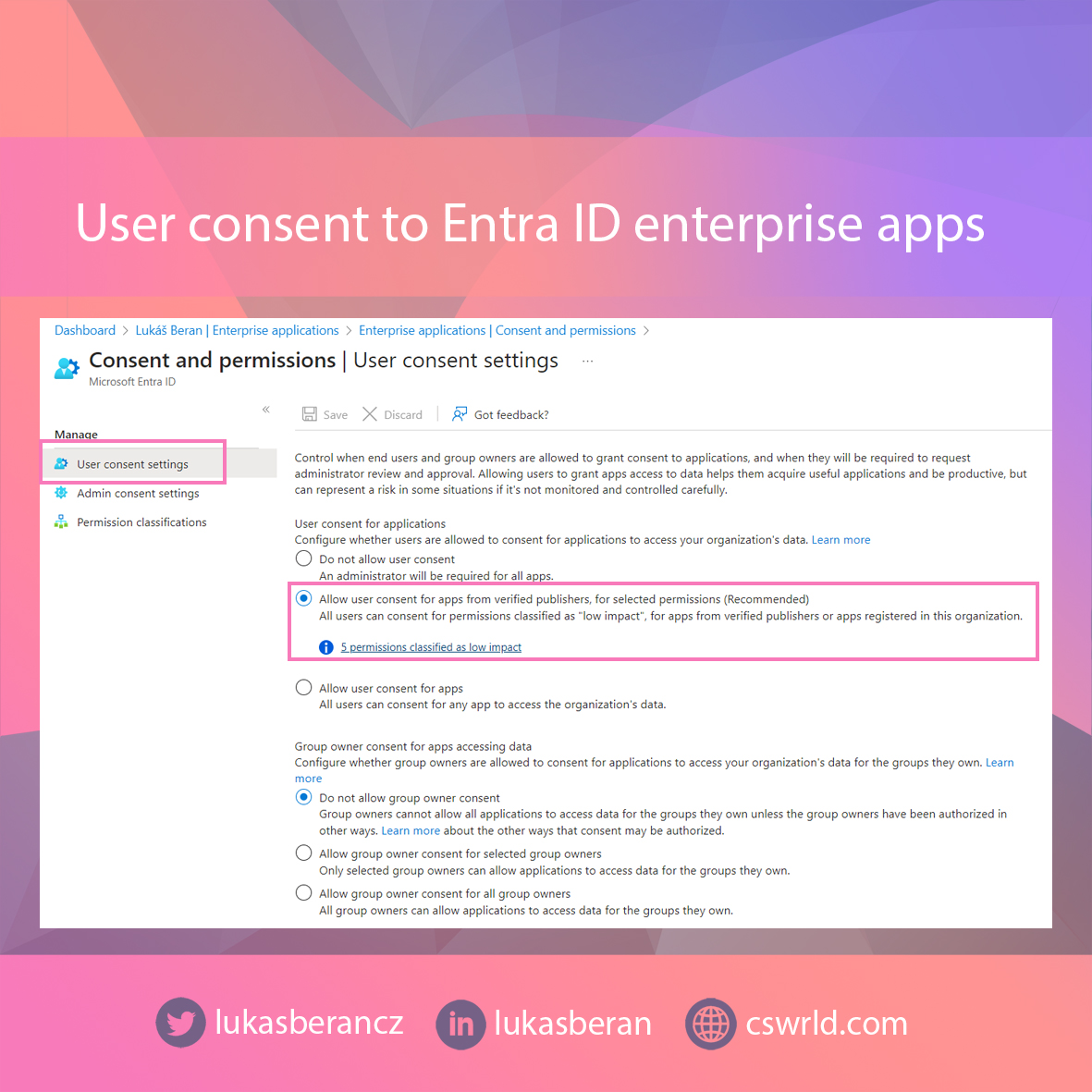
Restricting user consent permissions
For this reason, end-user permissions must be restricted. There are basically three scenarios, and it depends primarily on the needs of the organization which option it decides to go for.
- Users can give consent to applications that are from a verified publisher and with only minimal and pre-approved permissions. This option will only allow end users to give consent to trusted applications and only if they request some of the pre-approved low impact permissions.

- The second option is to not allow users to give consent to any application, but to allow them to request administrator consent. In practice, this means that if a user wants to use an application that has not yet been approved in Microsoft Entra ID, a window will appear giving the user the option to ask for admin consent. The administrator then receives, for example, a notification email and has a set period of time (up to 60 days) to approve. If the administrator does not approve the app in time, the request is automatically rejected.


- The third scenario is then to completely prohibit users from even just asking for approval. Thus, the user cannot make the application approval for themselves, nor do they have the option to ask the administrator for approval. This option is typical for organizations that have strict limitations and want to have enterprise applications fully under their control without the ability of users to interfere in any way.


In practice, the first option is the most common scenario for smaller organizations, where users can give consent to trusted applications themselves and can potentially ask an administrator for higher permissions if needed. This is because smaller organizations typically do not have enough administrators to take a more proactive approach to enterprise applications. Often these organizations have no in-house administrator, but only an external consultant.
For large organizations, it is recommended to block user consent altogether. And then it depends on whether the organization gives users the opportunity to at least ask for admin consent or not. Usually, however, requests for admin consent are also blocked, because it would mean a lot of extra work for administrators to handle user consent requests for all sorts of strange applications.
Final words
This article is not intended to discourage the use of enterprise applications. In fact, it’s the other way around, and using enterprise applications is very convenient because you have full control over those applications, user accounts, and the entire authentication process. Which is much better than having separate apps with separate accounts with no possibility of control.
You just need to adjust the default settings and deny unlimited consent to users. Which, unfortunately, is the default setting.





