Microsoft has come out with support for device-bound passkeys in Microsoft Authenticator as a method of Microsoft Entra ID authentication. Microsoft Authenticator is the only allowed software passkey at the time of writing this article. And only device-bound passkeys are allowed.
However, Microsoft is considering adding additional software passkeys that potentially don’t even need to be device-bound and could therefore be synchronized between multiple devices. However, this is still only a considered option in the current Preview phase and it is uncertain how/when/if this will ultimately play out in the future.
Only device-bound passkeys in Microsoft Authenticator are allowed at the time of writing this article.
This method is in Public Preview at the time of writing this article, so its capabilities and support are still subject to change.
Enable passkey authentication method in Microsoft Entra ID
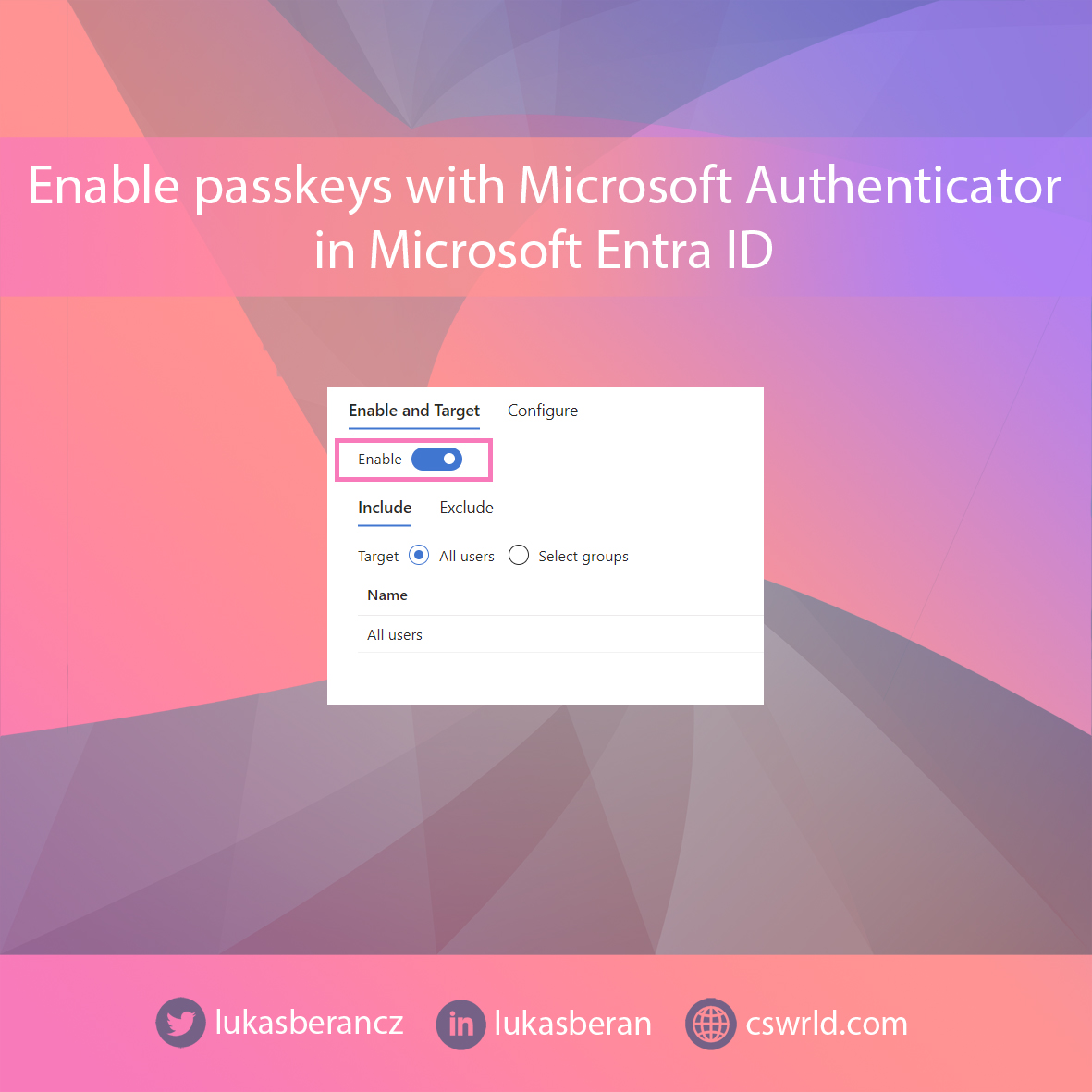
Open Microsoft Entra admin center and go to Protection – Authentication methods. Under Policies, open Passkey (FIDO2) and enable this method for all users or selected user groups. This enables the use of FIDO2 including passkeys within Microsoft Authenticator for the selected users.
Configure passkey authentication in Microsoft Entra ID
While the procedure described above is theoretically sufficient for Microsoft Authenticator to function as a passkey method for authentication, it is a good idea to set restrictions on what can be used as a passkey for authentication for Microsoft Entra ID.
So switch to the Configure tab. Passkeys in Microsoft Authenticator do not have attestation support at the time of writing this article, so you must turn off requiring attestation. However, Microsoft says that attestation support is planned for General Availability.
With the attestation requirement turned off, it is a good idea to set other restrictions in the form of allowing only specific Authenticator Attestation GUID (AAGUID) to be enabled for authentication to Microsoft Entra ID.
If you see a checkbox for Microsoft Authenticator (preview) in your tenant, you can just check that checkbox to enable the use of passkeys in the Microsoft Authenticator app for both Android and iOS. If you don’t see this checkbox in your tenant yet (like I do), you need to manually add the AAGUID for Microsoft Authenticator on Android and iOS.
- Microsoft Authenticator for Android:
de1e552d-db1d-4423-a619-566b625cdc84 - Microsoft Authenticator for iOS:
90a3ccdf-635c-4729-a248-9b709135078f

Get list of all FIDO2 keys used in the tenant
When you set restrictions via AAGUID above, you need to think about other FIDO2 devices used in the organization. If you allow only Microsoft Authenticator as mentioned above, all other FIDO2 devices would stop working. Even those already in use.
Therefore, it is important to add AAGUID of all other FIDO2 devices as well, if they are used in the organization. Ideally, you should add all the AAGUIDs of the models that you generally know are used in the organization. Check the manufacturer’s website or contact their support. For example, you can find AAGUIDs for Yubikey here.
It is also a good idea to list all the AAGUIDs that your users have already registered. You can do this easily via Microsoft Graph PowerShell.
How to get list of all FIDO2 keys registered in Microsoft Entra ID via PowerShell
First we need the Microsoft Graph PowerShell module installed.
Install-Module Microsoft.GraphWhen we have the Microsoft Graph module installed, we can connect to Microsoft Graph. We need AuditLog.Read.All and UserAuthenticationMethod.Read.All permissions, so we add this to the scope.
Connect-MgGraph -Scope AuditLog.Read.All,UserAuthenticationMethod.Read.AllAfter sucessfull authentication, you can get all FIDO2 keys registered for all of your users via the following command (credit goes to Nathan McNulty).
((Get-MgReportAuthenticationMethodUserRegistrationDetail -Filter "methodsRegistered/any(i:i eq 'passKeyDeviceBound')" -All).Id | ForEach-Object { Get-MgUserAuthenticationFido2Method -UserId $_ -All }).AaGuid | Select-Object -UniqueNow just make sure that the registered FIDO2 AAGUIDs are also on the allow list mentioned above.
How to register passkeys in Microsoft Authenticator
Registering passkeys in Microsoft Authenticator is pretty straighforward. You can either sign-in with your work or school account directly in the Microsoft Authenticator app which then automatically adds all enabled authentication options including passkeys.
Or you can go to https://aka.ms/setupsecurityinfo and add a new method from there.






